ITonDemand
Guide to Cybersecurity Maturity Model Certification (CMMC)
Information Security Compliance Standard to Defense Contractors / Vendors


What is CMMC?
The Cybersecurity Maturity Model Certification is a cybersecurity compliance certification intended to protect the supply chain of the Department of Defense and it’s vendors.
The CMMC was created by the DoD in response to rising malicious cyber activity that cost the U.S. economy between $57 billion and $109 billion in 2016. The DoD has issued the CMMC to protect Federal Contract Information or FCI and Controlled Unclassified Information or CUI.
In the DoD’s guide, these are defined as:
Federal Contract Information (FCI): FCI is information provided by or generated for the Government under contract not intended for public release.
Controlled Unclassified Information (CUI): is information that requires safeguarding or dissemination controls pursuant to and consistent with laws, regulations, and government-wide policies, excluding information that is classified under Executive Order 13526, Classified National Security Information, December 29, 2009, or any predecessor or successor order, or Atomic Energy Act of 1954, as amended.
The CMMC model uses the basic safeguarding requirements for FCI as the Federal Acquisition Regulation (FAR) Clause 52.204-21 and the security requirements for CUI as specified in NIST 800-171 / DFARS.
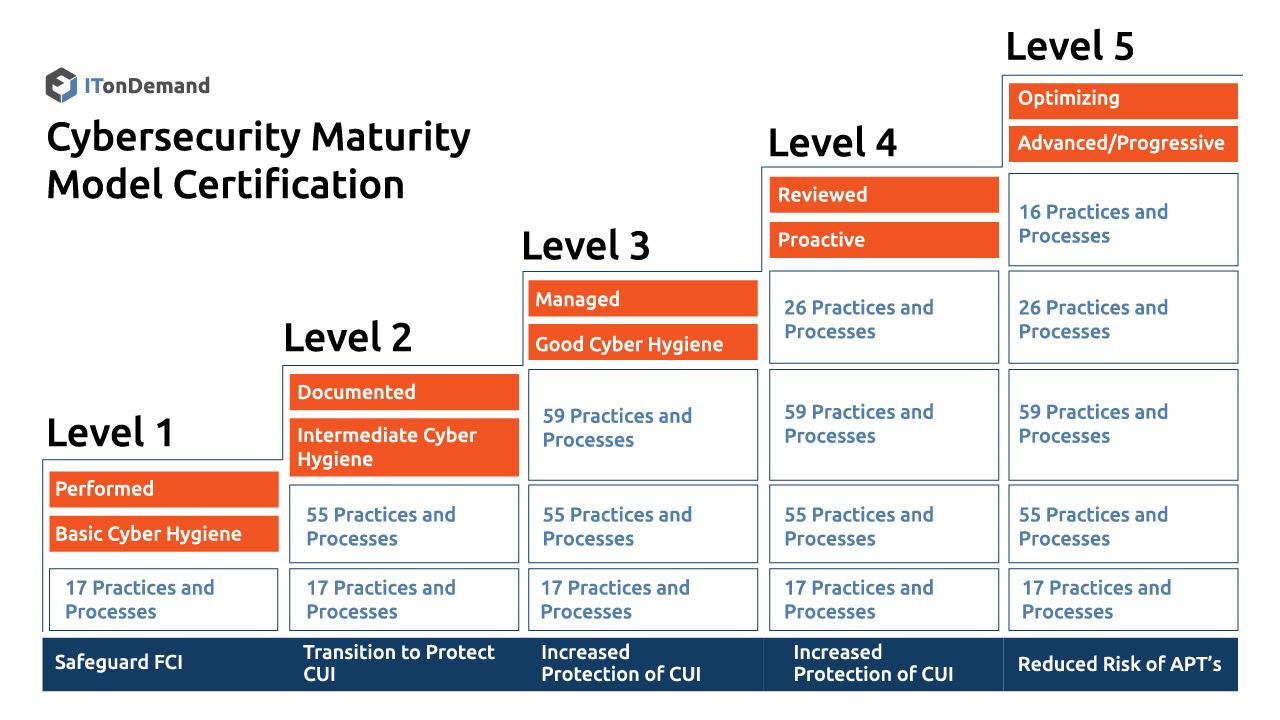
CMMC Levels Explained

The Five Levels of CMMC
The CMMC measures cybersecurity maturity with five levels and aligns a set of processes and practices with the type and sensitivity of the information to be protected and the associated range of threats.
Level 1: Safeguard Federal Contract Information (FCI)
Level 2: Serve as a transition step in cybersecurity maturity progression to protect CUI.
Level 3: Protect Controlled Unclassified Information
Level 4-5: Protect CUI and reduce risk of Advanced Persistent Threats
These levels of certification are achieved by Processes and Practices as defined in the CMMC.
CMMC Level 1
-
Processes: Performed
Level 1 of CMMC requires an organization to perform specified practices. The organization may perform them as necessary without formal documentation.
-
Practices: Basic Cyber Hygiene
Level 1 is primarily concerned with the protection of FCI and corresponds to the basic safeguarding requirements found in FAR 52.204-21, referenced above.
CMMC Level 2
-
Processes: Documented
Process documentation ensures that necessary security and hygiene practices are performed in a “repeatable manner”.
-
Practices: Intermediate Cyber Hygiene
Level 2 serves as a transition stage between 1-3 of CMMC. The practices necessary are a subset of NIST 800-171 as well as other standards. This stage includes the hygiene and security of CUI.
CMMC Level 3
-
Processes: Managed
Level 3 requires organizations to have resources devoted to the management of practice implementation.
-
Practices: Good Cyber Hygiene
Level 3 of CMMC focuses on the protection of CUI. It encompasses NIST-800 as well as other standards for threat mitigation. DFARS contains additional requirements beyond NIST, like incident reporting.
CMMC Level 4
-
Processes: Reviewed
Level 4 includes a review of past practices for effectiveness. This also includes notification of higher-level management of status or issues on a periodic basis.
-
Practices: Proactive
Level 4 practices protection of CUI from Advanced Persistent Threats or APTs. It includes NIST SP 800-171B and includes enhanced detection and response capabilities.
CMMC Level 5
-
Processes: Optimizing
Level 5 requires an organization to take corrective action towards improving process implementation across the organization.
-
Practices: Advanced/Proactive
Level 5 increases the depth and sophistication of cybersecurity capabilities.

CMMC Domains
CMMC consists of 17 domains with the majority originating from the Federal Information Processing Standards (FIPS) and NIST 800-171. CMMC includes three additional domains not included in those standards.
- Access Control (AC)
- Asset Management (AM)
- Audit and Accountability (AU)
- Awareness and Training (AT)
- Configuration Management (CM)
- Identification and Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PE)
- Recovery (RE)
- Risk Management (RM)
- Security Assessment (CA)
- Situational Awareness (SA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)
CMMC ascribes 173 points across these 17 families and assigns them to the 5 levels accordingly.
For a full list of the CMMC requirements, click here to download their PDF.

What is our approach to compliance?

Compliance Audit
Our team conducts a series of interviews and a network audit to determine data access and usage.

Gap Analysis
A Gap Analysis identifies the missing pieces necessary to achieve compliance.
Remediation Plan
A remediation plan is put forth and executed with action steps towards compliance based on priority level.

Management
ITonDemand then monitors system usage and provides the service and support to maintain compliance.
Compliance+ in Action / Florida Manufacturing Firm
A small north Florida manufactures CNC close tolerance machined parts, custom components, and assemblies for the defense sector. Given the sensitive nature of the parts being manufactured, it was vital that communications and manufacturing specifications were secure while organizational infrastructure was put in place and maintained to NIST Compliance.
Read how ITonDemand made it happen.


Contact Us
