While many cyber threats come in and out of popularity, spear phishing is always in season. It’s an effective way to target specific people or businesses with a focused attack to gather sensitive data. Just last year, phishing attacks surged by over 47%, and that trend will only continue for as long as hackers are finding success.
The risk isn’t just for small businesses, either. When an organization has tens of thousands of employees, even with strong cybersecurity, managing each person’s habits becomes increasingly difficult. All it takes is one person to give sensitive info to the wrong person or click the incorrect link, which can cause irreversible damage. That’s why it’s increasingly important for companies to be aware of threats that target employees and have a plan to protect against them.
Table of Contents
How Do Spear Phishing Attacks Differ From Standard Phishing Attacks?
What’s an Example of a Spear Phishing Attack?
Using Public Information Can Make Messages Convincing
Spam Filters Struggle With Spear Phishing Attacks
AI Is Being Used To Make More Realistic Phishing Messages
9 Ways To Protect Yourself From Spear Phishing
Conclusion
What Is a Spear Phishing Attack?
Spear phishing is a targeted phishing attack aimed at specific people or businesses and is usually done via email or text. They’re designed to steal sensitive information, like login credentials or credit card details. They may also ask for money or gift cards directly. Stolen information may be used, sold, or act as a staging point for a larger attack. Since spear phishing is more personalized, they often pretend to be friends, family members, or a high-level individual at an organization.
How Do Spear Phishing Attacks Differ From Standard Phishing Attacks?
Phishing and spear phishing are both cyber threats designed to trick people into giving away sensitive information, but they are executed quite differently. The main difference between the two is the scale of the attack. In fishing terms, a standard phishing attack is like casting a wide net across the internet. Since there’s no focus, they’re often not very convincing. That means what’s caught isn’t predictable, but a handful of people may still fall for it since it’s done on such a large scale.
In contrast, spear phishing is likened to throwing a spear at a specific target with intent. In those situations, the attacker is often after specific information with a greater goal in mind. As a result, much more planning may be involved to make messages more convincing. As a result of the extra effort, spear phishing attacks have a greater success rate, but they can only be used to target a limited number of people or organizations.
What’s an Example of a Spear Phishing Attack?
One of our staff members was recently contacted in an attempted spear phishing attack. The threat actor pretended to be the CEO and said they were on a call with a client. Client meetings happen frequently in the IT industry, so it was a plausible start to the story. You can see an example below of what that looked like:
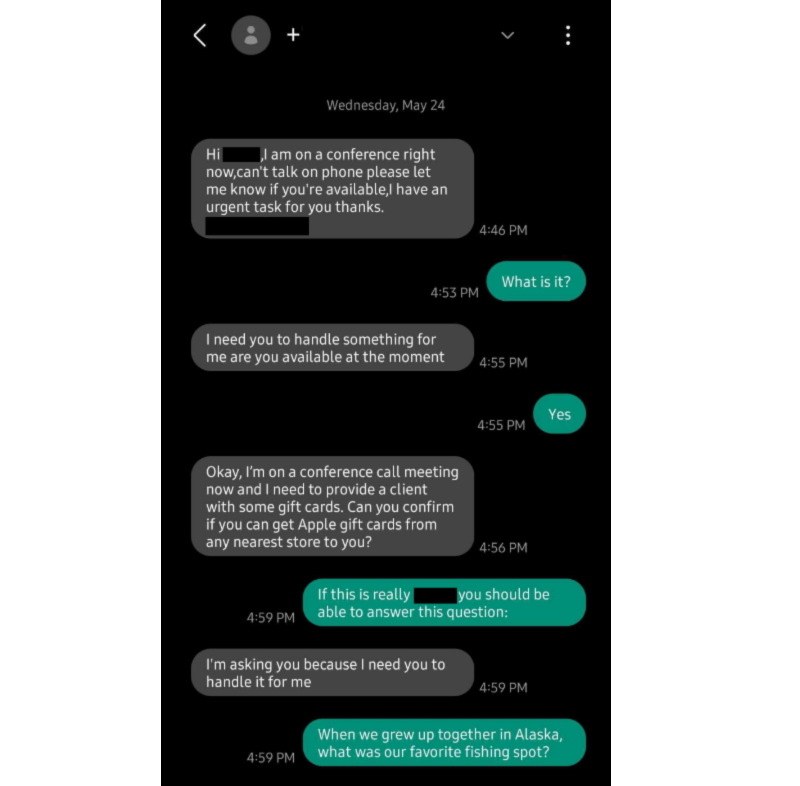
The attack wasn’t as well researched as some. They ran with minimal information and weren’t prepared for much pushback or discussion. There were a couple of different red flags about this message, which you should keep in mind any time you get a sudden unusual request by someone that claims to be someone you know:
- It came from an unknown number. Due to that, there was no contact picture either.
- The message didn’t have the writing style of the person they were pretending to be.
- They urgently requested gift cards, which is a common scam tactic.
- The person they contacted is not someone who would be handling this type of request.
The attacker wasn’t fully vested and was likely testing the waters. Since they were caught onto right away, with the not-so-subtle question about Alaskan fishing, they likely viewed it as not worth the effort. Because of that, it’s worth highlighting another key point: cybersecurity awareness can prevent many attacks because many are only after targets that they can trick easily.
Using Public Information Can Make Messages Convincing
The most effective spear phishing attacks involve gathering personal information that’s available publicly, like location, family names, work history, etc., to create familiarity. People post a lot of their life online via social media accounts. There’s also a lot of personalized company and employee data on sites like ZoomInfo and LinkedIn.
With enough research, an attacker may know everything from former co-workers to the names of pets. When reaching out, they may reference specific pieces of knowledge that are available publicly. Successful phishing attempts or other strategies like social engineering are also used to gather information to jump-start further attacks.
Spam Filters Struggle With Spear Phishing Attacks
Spam filters are meant to recognize and filter out phishing messages. They can identify characteristics they usually have, along with bulk mailing patterns, to prevent them from being delivered. However, with spear phishing, since the message is more personalized and may be unique to each target, they don’t share any behavior or content patterns. That makes them very hard for spam filters to detect or stop.
AI Is Being Used To Make More Realistic Phishing Messages
Writing has always been a weak point for threat actors, with messages rarely convincing anyone but gullible or distracted people. Even if AI has hit a wall, it’s made significant advancements in the past few years. It can write clear and confident-sounding messages, even if they’re not entirely true. Through creative input, it can even take on different writing styles, tone of voice, and roles within a company to better copy personalities. It can make persuasive messages when used well, increasing the success rates of well-planned attacks.
9 Ways To Protect Yourself From Spear Phishing
While spear phishing can be an effective tactic, there are many ways to reduce the chance of success and the damage done. Here are nine ways that you and your business can protect yourself:
Cybersecurity Awareness
Cybersecurity awareness, which can involve reading content like this, is one of the best ways to avoid falling prey to phishing attacks. If you know what one looks like and some red flags, you’re less likely to fall for any attempt.
Simulated Phishing Training
Giving staff hands-on experience with simulated phishing training is a safe and educational way to let people experience it for themselves. It involves receiving fake phishing emails, which tell the user it’s not real if the links are followed. It also provides guidance and tips along the way.
Advanced Anti-Spam Tools
Most email, text, and phone services come with some degree of spam filtering that can prevent basic phishing attempts. However, more advanced anti-spam solutions can help detect spear phishing attempts, such as noticing an odd request from someone not within a company or on anyone’s contact list.
Multi-Factor Authentication (MFA)
MFA can’t stop spear phishing directly, but it can help protect accounts from unauthorized access. The most common use requires a passcode sent to the user’s phone via text. That means even if the login credentials are stolen, an attacker can’t log into an account without access to the extra layer of security.
Data Access Controls
When employees have free access to everything, every account is a point of weakness for cyberattacks. With data access controls, employees only have the permissions and access they need for their work and nothing more. If a breach happens, it greatly limits the extent of the damage.
Incident Response Plan
While all businesses hope to never become a cyberattack victim, with 81% of organizations seeing an increase in phishing attacks, it’s an ongoing risk. An incident response plan means that even if an attempt is successful, the damage done is limited through a quick response time and pre-planned strategy.
Data Security Policies
It’s common for larger businesses to have data security policies to protect both the organization and the customers. However, many smaller companies don’t have any in place. Not only does that greatly increase risks, but it can also leave some owners legally liable if their IT doesn’t comply with their industry.
Don’t Be an Easy Target
There are many ways to protect yourself from spear phishing, and most of them can be described in one way: don’t be an easy target. By doing some of the above strategies and being aware of different types of threats, most scammers will think it’s more work than it’s worth. If they lose patience, they’ll move on to an easier target.
Hire an MSSP
A managed security services provider (MSSP) can provide companies with a wide range of cybersecurity services. That includes some of the methods discussed above, including phishing training, MFA, anti-spam tools, controlling data access, creating security policies, and developing a response plan.
Conclusion
Spear phishing is more than a cyber threat; it’s a human-focused strategy that leverages trust and familiarity to breach defenses. Understanding how these attacks work, along with some of the red flags, can greatly reduce the chance of falling for them. That’s made cybersecurity awareness and phishing training effective strategies to counter phishing attempts. However, even well-informed people can get tricked by it, especially during a busy workday.
IT security teams can do work on the backend to help too. Limiting account access to only needed services reduces the damage any one breach can do. MFA, anti-spam tools, and incident response planning can further decrease that. But there’s only so much that security experts can do. Ultimately, the best defense against spear phishing is our own. Be careful with clicking, be skeptical of strange requests, and when in doubt, contact the person you know directly through a different method.
Is your business concerned about spear phishing, or have you already experienced a data breach? Let us fortify your cybersecurity. For a consultation, please use our contact form or call us at +1 (800) 297-8293




