Crypto malware attacks have started to pick up again, as hackers distribute it through methods like fake google chrome updates where users are prompted to download an infected file. Cryptocurrency has declined since Bitcoin (BTC) peaked at over $67,000 in November 2021, but has rebounded over the past few months. While the total market cap hit a 2-year low of $826.51 billion in December 2022, it has improved to $1.13 trillion as of May 2023.
Like with stocks, prices continue to fluctuate, as it’s used for both private transactions and speculative investing. Being able to make anonymous payments, and bypassing traditional banks, has made it profitable for criminals too. Crypto malware allows hackers to farm the currency using their targets’ computers. Not only does it slow down devices that are unknowingly mining it, but it also greatly shortens its lifespan through high usage. To avoid becoming a victim, it’s essential to understand what cryptocurrency is, why hackers may want it, and how to avoid getting infected by crypto malware.
Table of Contents
How Does Crypto Mining Work?
Crypto Malware vs Ransomware
How To Detect Crypto Mining
How To Remove Crypto Malware
How To Avoid Getting Infected With Crypto Malware
A Brief History of Cryptocurrency
Why Cryptocurrency Is Popular With Hackers
Protect Yourself From Crypto Malware With ITonDemand
What Is Crypto Malware?
Crypto malware, also known as cryptojacking, is a type of malware that uses other people’s computers to mine cryptocurrency without being detected. That currency can be converted into more traditional money forms like USD. It’s usually spread through phishing emails, pop-up ads, fake websites, or applications. From there, users are prompted to download the infected file, where upon opening, the crypto malware installs itself and actively runs in the background. It can also create a backdoor for other malware to be loaded onto the device.
How Does Crypto Mining Work?
Crypto mining is the process of generating cryptocurrency by converting a random series of letters and numbers into an output that rewards a block of that currency. Solving it requires a computer and is most comparable to a dice roll due to the luck involved. The more people mining, the more competition there is for the same currency block. Computers with more computing power, or people who use multiple devices at once, are getting more dice rolls by making calculations faster.
With crypto malware, hackers use other people’s computers instead of their own to farm cryptocurrency. The main cost of crypto mining is electricity because computers run at full power while making these calculations. While electricity isn’t always worth the value of cryptocurrency, hackers are profiting by not using their own for mining.
Crypto Malware vs. Ransomware
The main difference between crypto malware and ransomware is the prior uses your computer to mine cryptocurrency, while the latter holds data hostage and requests cryptocurrency that has already been mined.
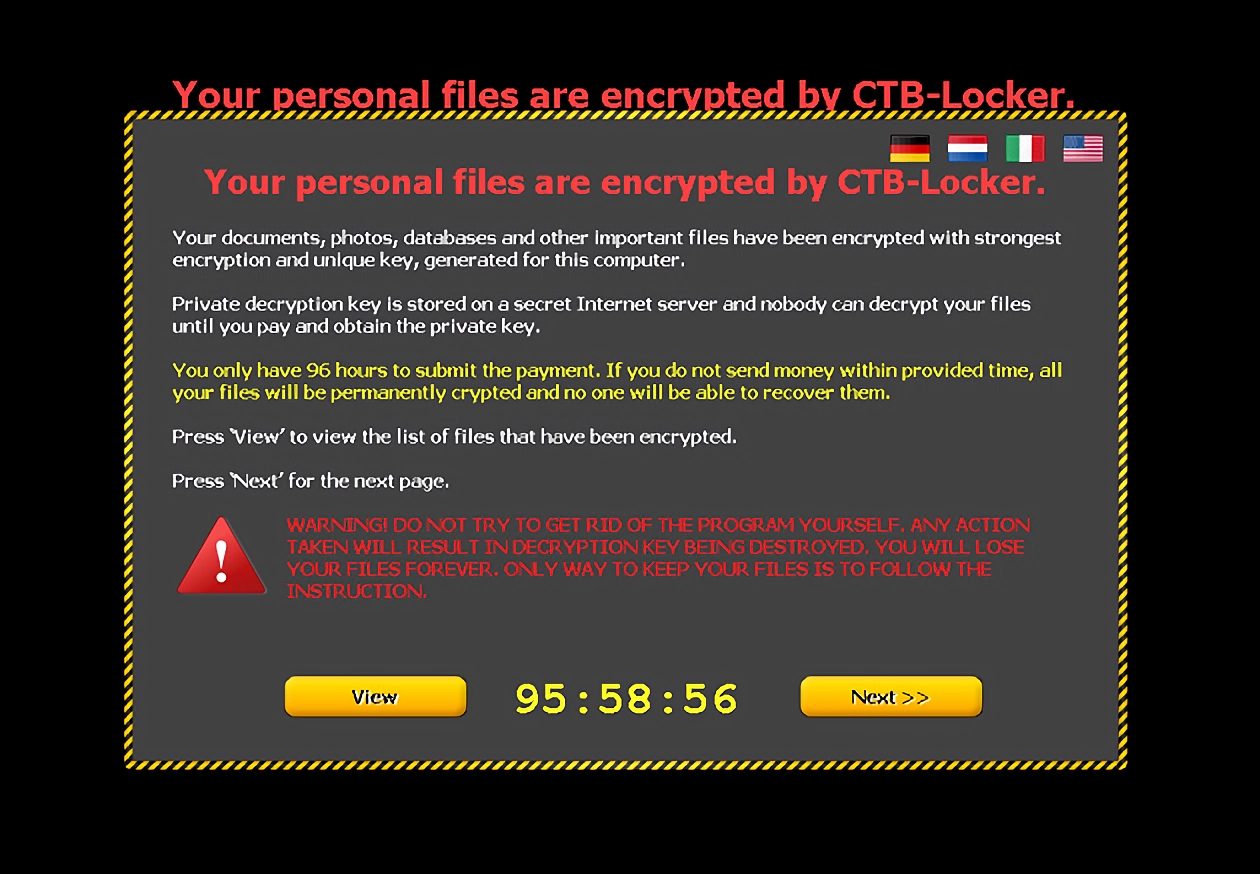
While crypto malware may not directly take money or personal files from a target, they’re indirectly profiting by draining a computer’s resources and lifespan and increasing the user’s electricity bill. On the other hand, ransomware blackmails for money upfront and may threaten to delete valuable files if not done quickly enough.
How To Detect Crypto Mining
Since malware that does crypto mining runs passively in the background, it can take some extra detective work to discover. There are many signs, like performance issues, laptop batteries draining quickly, high CPU usage, increased electricity bills, and unusual background processes in the task manager.
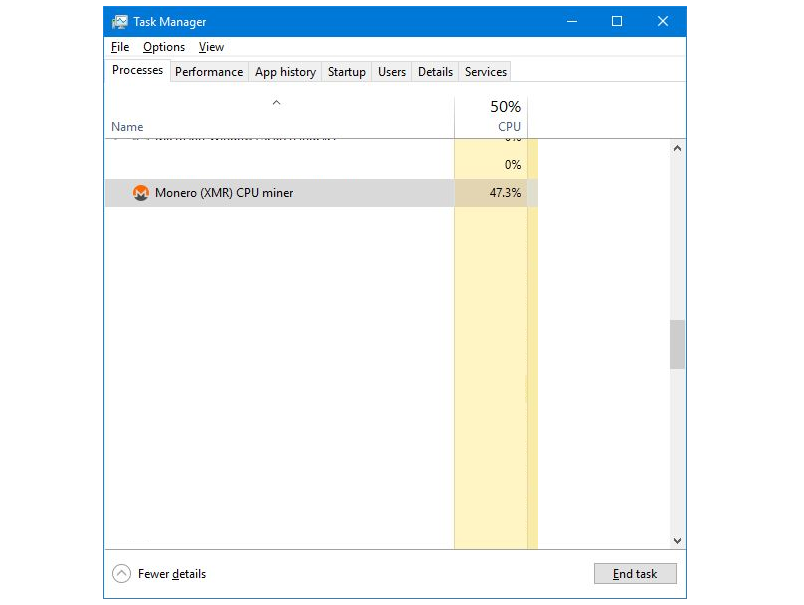
Some forms of crypto malware are more difficult to detect than others. Anti-malware software can help prevent and catch it, but other types require an IT security expert to find it. Remember, a slow computer doesn’t mean it’s infected with malware, a virus, or some other threat. Some computers are configured poorly, have outdated software, or are getting old.
How To Remove Crypto Malware
Even if you’ve identified that your computer is infected with crypto malware, removing it is not always easy. It’s always recommended to reach out to an IT company first, as they can ensure the device gets scrubbed of all malicious files, preventing it from reinstalling itself. However, if that’s not an option, here are some steps you can try on your own:
1. Identify the Crypto Malware
Once you know what type of crypto malware it is, you can usually find more information online. That can include seeing how the installation process works and what the mining process looks like. You can also access the cryptocurrency’s website for additional help.
2. Disconnect From the Internet
Crypto malware can’t fully function without an internet connection, so that stops it from sending data online. Depending on the type of malware, it also reduces the chance of it being able to reinstall itself and prevents your computer from being remotely accessed by a hacker.
3. Enable Safe Mode
Once your device is disconnected from the internet, enter safe mode. For Windows computers, press the F8 key repeatedly until the Windows logo appears. Under advanced boot options, choose “Safe Mode with Networking.” If using a Mac, restart the computer and hold the shift key until the Apple logo appears.
4. Scan Your Computer
Use antivirus or anti-malware software to do a complete scan of your computer. Follow the prompted steps to isolate the infected files and remove them. It may not always show up depending on how the crypto malware is configured.
5. Delete Suspicious Programs
If the malware-installed mining software links to the hacker’s wallet and does nothing else, it may appear as a standard installed program. Delete any suspicious ones you find. If uncertain about which programs are safe, search for more information online or consult an IT specialist.
How To Avoid Getting Infected With Crypto Malware
A good defense against crypto malware is cybersecurity awareness. That means if you’ve been reading our blog, you’ve already taken an excellent first step. It’s important to be careful when downloading files off the internet. Something as innocent as an HTML document can be infected with malware, ransomware, viruses, or other types of attacks. Make sure your antivirus and anti-malware stay up-to-date, and use auto-updating options when possible since it’s easy to forget.
A Brief History of Cryptocurrency
Cryptocurrency, a secure form of digital currency, began with the release of Bitcoin in 2009. Payments are made through an encrypted peer-to-peer electronic cash system, bypassing financial institutions and the safety nets they can provide. Its goal was to offer a decentralized form of currency that wasn’t tied to any bank or country. There are some risks involved, though. Losing access to the digital wallet leaves no option to recover lost money. Also, cryptocurrency values can drastically change month-to-month, making them less stable than traditional currencies like the US dollar.
Bitcoin’s wide usage led to the creation of many more cryptocurrencies like Ethereum, Tether, BNB, XRP, and Monero, the latter being involved in recent crypto malware attacks. While some countries like China have banned them, others have tried establishing guidelines and regulations to manage their usage. Due to the challenge of connecting people with transactions, they’re still a popular way to exchange money. However, software developers have created ways to track transactions through digital wallet IDs, so identifying fraudulent behavior is becoming easier.
Why Cryptocurrency Is Popular With Hackers
While there are ways to track other people’s cryptocurrency wallets and link them to specific people, it’s still more anonymous than many forms of transactions. The fact it’s easy to use, globally available, and lacks regulations makes it harder for authorities to differentiate fraudulent payments from real ones. Furthermore, since mining malware is used to generate cryptocurrency for the hacker, and it’s not taken directly, it’s harder to track than ransomware.
Protect Yourself From Crypto Malware With ITonDemand
Crypto malware continues to be a widespread attack of choice for hackers worldwide. The lack of regulations and ease of installation makes hiding easier than some types of cyber-attacks. Additionally, because nothing is being stolen besides the target’s electricity and computing power, they can profit from others with little risk to themselves.
Choosing a cybersecurity partner like ITonDemand can help protect you and your business from crypto malware. With access to IT security experts, you can ensure you have the best threat detection and can stop most risks before they even reach your inbox. And if an employee does make a mistake, you’ll have access to an incident response team to handle any challenge that comes your way.
Are you or your business concerned about crypto malware and other cybersecurity threats? Reach out for a consultation through our contact form or call us at +1 (800) 297-8293




